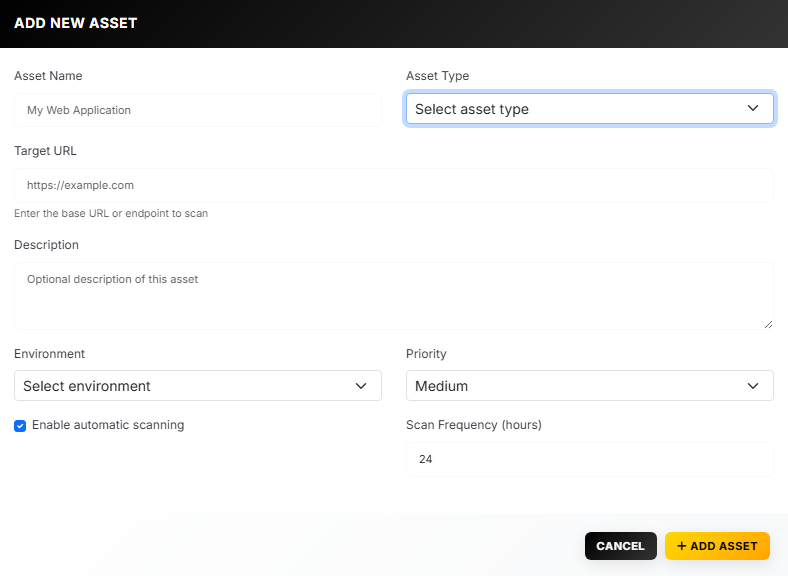
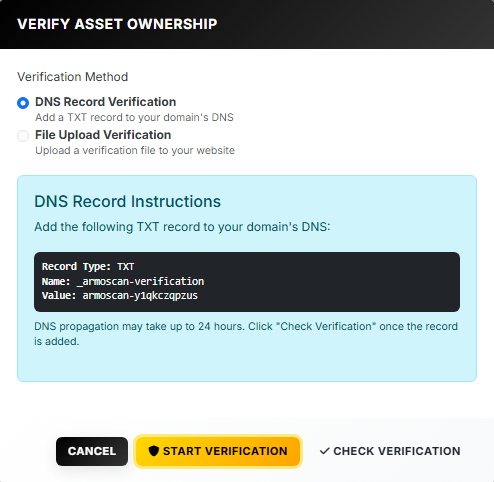
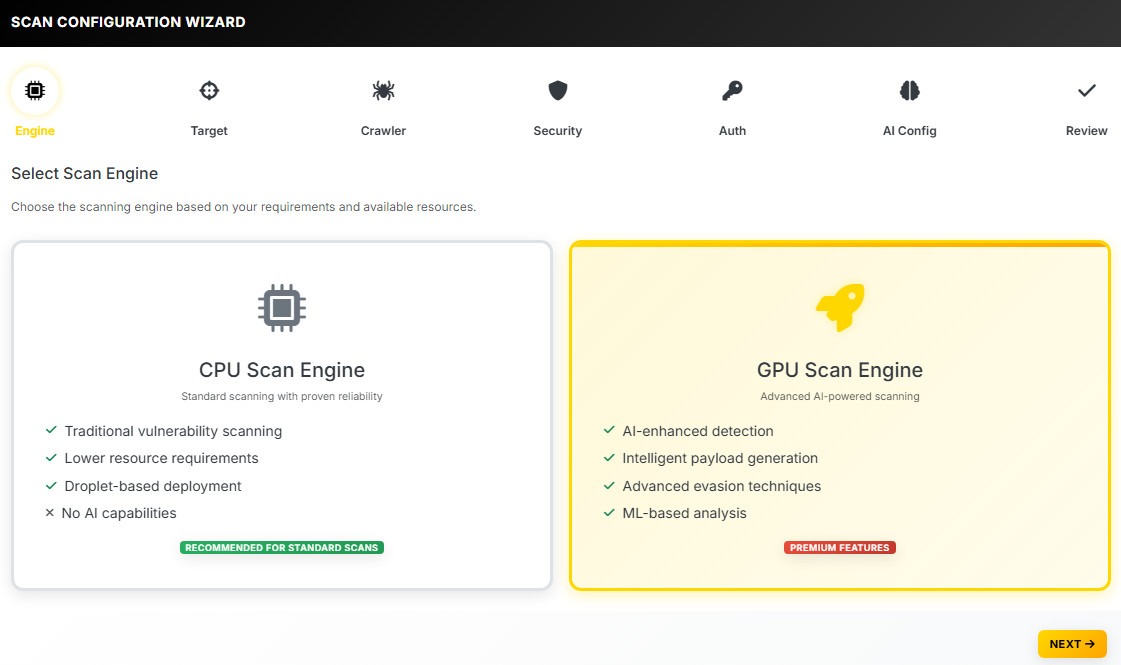
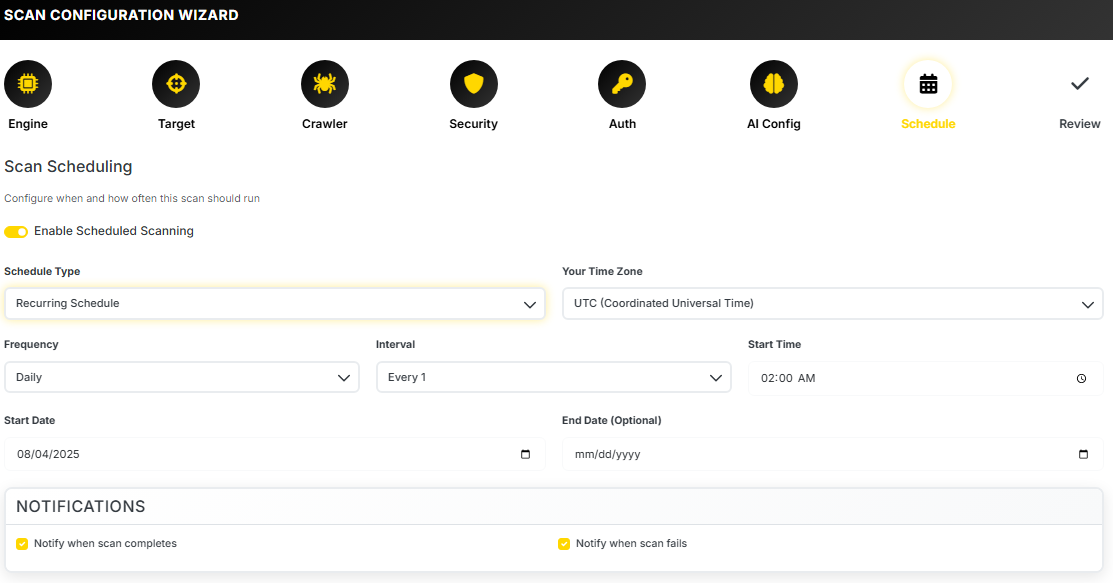
AI Powered Vulnerability Scanner
Next-generation security platform leveraging artificial intelligence and distributed computing to deliver unparalleled vulnerability detection, zero-day threat discovery, and automated remediation across enterprise infrastructure.
247
Threats Detected
99.2%
Accuracy
0.3ms
Response Time
AI Neural Engine: ACTIVE
Threat Detection: SCANNING
Auto Remediation: READY
ENTERPRISE READY
Ready to Experience AI-Powered Security?
Join Fortune 500 companies and government agencies who trust ArmoScan Enterprise for mission-critical security assessment and compliance management.
SOC 2 Type II Certified
Enterprise-grade security
24/7 Expert Support
Dedicated customer success
99.9% Uptime SLA
Mission-critical reliability